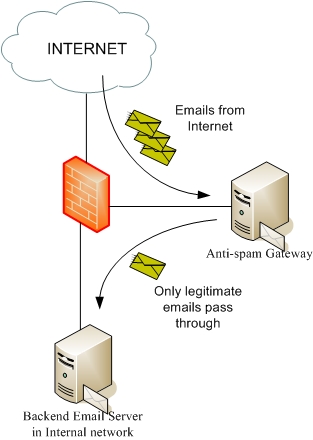
In this tutorial i’ll show how to ensure and apply many feature for our mail gateway try to avoid most of the mail spam. I’ll explain all the options that we’ll setup to understand it and modify it to any scenario. For this tutorial I used a machine with Centos 6.0 with the postfix mail software and other virtual machine Debian Squeeze running bind9 for DNS request. We’ll configure SPF (sender profile framework) to check the DNS records txt for check which servers are allowed to send mails with the domains that we’ll received mails in our servers, also we’ll configure some RBL to check in real time server black list and avoid these servers.
1.- Install postfix and setup to autostart service:
# yum install postfix # chkconfig --levels 235 postfix on
2.- Edit some options for ensure our mail server and avoid a lot of spam:
# vi /etc/postfix/main.cf
myhostname = mail.mydomain.com #host name
myorigin = mydomain.com #Domain name for mail senders
mydestination = mydomain.com #Local domains
mynetworks = 127.0.0.1/32, 192.168.1.0/24 # Networks that are allowed to send
inet_interfaces = localhost, 192.168.1.200
relay_domains = hash:/etc/postfix/relay_domains #File with accepted domains
parent_domain_matches_subdomains = debug_peer_list smtpd_access_maps #Not accept subdomains
smtpd_recipient_restrictions = reject_unauth_destination #Deny domains that are not included in relay_domains check_policy_service unix:private/policy #Check SPF policy reject_unauth_pipelining reject_unknown_sender_domain #Deny the request for the mail from address for non exist domain name reject_unknown_recipient_domain #Deny the request for the rcpt to address for non exist domain name reject_invalid_hostname #Deny the helo request for invalid FQDN host name reject_non_fqdn_helo_hostname #Deny the helo request for non exist FQDN host name reject_non_fqdn_sender #Deny the request for mail from address that don't follow a FQDN reject_non_fqdn_recipient #Deny the request for rcpt to address that don't follow a FQDN permit_mynetworks #Allow send mails from our network
smtpd_banner = $myhostname Microsoft ESMTP MAIL service ready
smtpd_helo_required = yes
3.- Edit the file relay_domains to add the domain names that are allowed for send mails to our server:
# vi /etc/postfix/relay_domains mydomain.com OK
4.- Compile our relay_domains file:
# postmap /etc/postfix/relay_domains
5.- Configure SPF in our domain (192.168.1.57):
@ IN TXT "v=spf1 mx ip4:192.168.1.200/24 ~all"
6.- Configure spf in postfix:
# yum install perl-CPAN wget perl-NetAddr-IP perl-Module-Build perl-Test-Base perl-Net-DNS perl-Net-DNS-Nameserver
# perl -MCPAN -e shell
cpan[1]> install Net::DNS::Resolver::programmable
cpan[2]> install Error
cpan[3]> q
# perl -MCPAN -e "get('Mail::SPF')"
# cd /root/.cpan/sources/authors/id/J/JM/JMEHNLE/mail-spf
# tar -xzvf Mail-SPF-v2.8.0.tar.gz
# cd Mail-SPF-v2.8.0/
# perl Build.PL
# ./Build
# ./Build test
# ./Build install
7.- Download spf software and setup postfix:
# wget https://launchpad.net/postfix-policyd-spf-perl/trunk/2.009/+download/postfix-policyd-spf-perl-2.009.tar.gz # tar -xzvf postfix-policyd-spf-perl-2.009.tar.gz # cp postfix-policyd-spf-perl-2.009/postfix-policyd-spf-perl /usr/libexec/postfix/postfix-policyd-spf-perl # vi /etc/postfix/master.cf policy unix - n n - - spawn user=nobody argv=/usr/bin/perl /usr/libexec/postfix/policyd-spf-perl
8.- Configure database RBL (Realtime Blackhole List):
# vi /etc/postfix/main.cf smtpd_recipient_restrictions= ... reject_rbl_client zen.spamhaus.org reject_rbl_client relays.ordb.org reject_rbl_client blackholes.wirehub.net reject_rbl_client list.dsbl.org permit_mynetworks
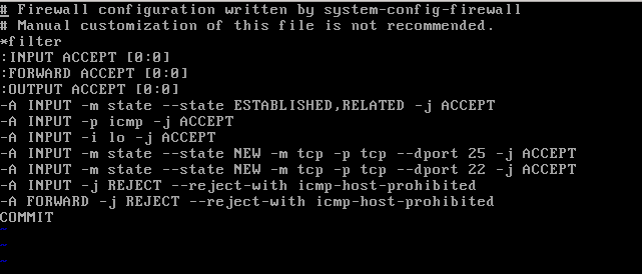
8.- Add Iptables rule:
# vi /etc/sysconfig/iptables -A INPUT -m state --state NEW -m tcp -p tcp --dport 25 -j ACCEPT
9.- Restart services postfix and iptables:
# service iptables restart # service postfix restart
Test our configuration postfix:
– forces to use ehlo to establish a connection with mail server:
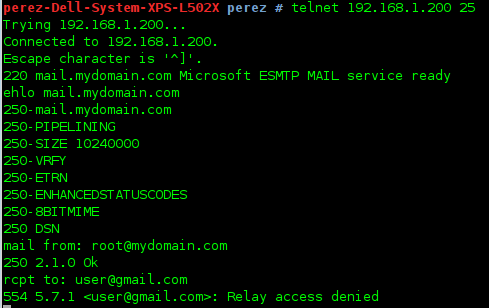
– Domains don’t listed in relay_domains file are not allowed to send mails with our server:
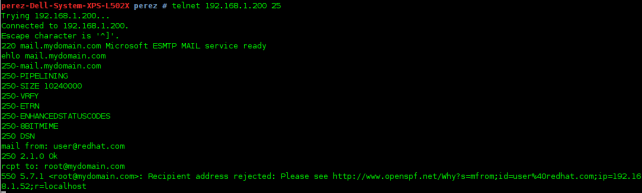
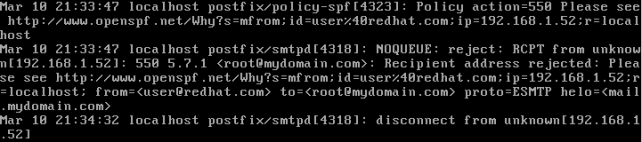
– check SPF records and reject non valid mails from other servers:
logs for spf: